End-to-end encryption (E2EE)
E2EE is a method of secure communication that prevents third-parties from accessing data while it’s transferred from one end system to another. This means that even the service provider or the platform facilitating the communication cannot access the data. In the context of storing end-to-end encrypted data in a SQL database, here are some common approaches:
-
Store Encrypted Data as Blobs:
- One common approach is to treat the encrypted data as a binary large object (BLOB) and store it in the database. The encryption and decryption processes are handled outside the database, typically by the application or client software.
- The application encrypts the data before storing it in the database and decrypts it when retrieving it. The database itself is unaware of the encryption key or the contents of the encrypted data.
-
Application-Level Encryption:
- Encryption and decryption are handled at the application level before data is stored in or retrieved from the database.
- The application is responsible for managing the encryption keys securely. The database stores only the encrypted data, and the encryption process is transparent to the database.
-
Column-Level Encryption:
- Some database systems provide built-in support for column-level encryption. In this approach, only specific columns containing sensitive data are encrypted.
- The database system manages the encryption and decryption of these specific columns, and the keys are managed either by the database itself or an external key management system.
-
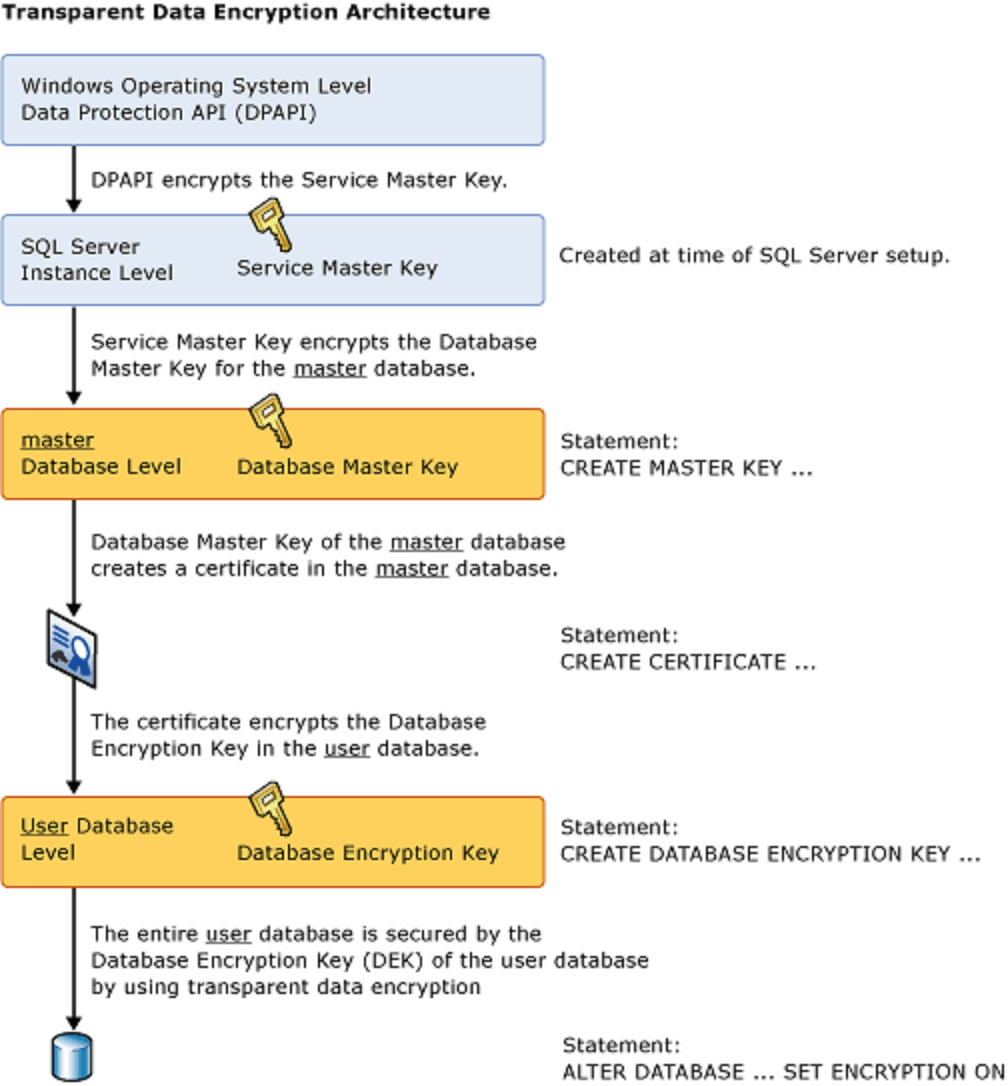
Transparent Data Encryption (TDE):
- Certain database systems offer features like Transparent Data Encryption, which automatically encrypts data at rest on the storage media. This protects the entire database, but it’s not end-to-end encryption in the traditional sense.
- TDE encrypts the data on disk, and when the data is read into memory for processing, it is automatically decrypted by the database engine. This can protect against unauthorized access to the physical storage media.
It’s crucial to note that regardless of the approach, managing encryption keys securely is a critical aspect of maintaining the security of the encrypted data. If an attacker gains access to the keys, they could decrypt the data. Key management solutions, hardware security modules (HSMs), or secure key storage practices are often used to enhance the security of encryption.
Let’s discuss the security, contact us.
Note : TDE protects data at rest, which is the data and log files. It lets you follow many laws, regulations, and guidelines established in various industries. This ability lets software developers encrypt data by using AES and 3DES encryption algorithms without changing existing applications. Check “Configure SQL Server Database Engine for encrypting connections”